SmartLoader Clones Oura Ring MCP to Deploy Supply Chain Attack
A sophisticated supply chain attack targeting the MCP ecosystem used fake GitHub accounts and a cloned Oura Ring server to infiltrate developer environments with credential-stealing malware.


Signal Check ⚡️
EXECUTIVE SUMMARY OF FINDINGS
Straiker's AI Research (STAR) Labs team has uncovered a trojanized MCP server targeting Oura Ring health data and successfully infiltrated legitimate Model Context Protocol (MCP) registries, exposing thousands of developers and end-users to credential theft and data compromise. SmartLoader, an established malware operation known for distributing info-stealers through deceptive installers, first discovered early in 2024, has constructed an elaborate network of fake GitHub accounts and repositories to distribute trojanized MCP servers, successfully poisoning legitimate MCP registries in the process.
Our investigation revealed the threat actors cloned a legitimate Oura MCP Server—a tool that connects AI assistants to Oura Ring health data—and built a deceptive infrastructure of fake forks and contributors to manufacture credibility. The trojanized version of the Oura MCP server delivers the StealC infostealer, targeting developer credentials, browser passwords, and cryptocurrency wallets.
This campaign signals a significant shift in the threat landscape: traditional threat actors who have long targeted software supply chains are now pivoting to MCP ecosystems, bringing their proven tactics and operational sophistication to this emerging attack surface.
Key Findings:
What happened? SmartLoader poisoned legitimate MCP registries with a trojanized Oura MCP Server designed to steal credentials, cryptocurrency, and health data.
How did they do it?
- Created at least 5 fake GitHub accounts to build a network of seemingly legitimate repository forks
- Added fake accounts as "contributors" to manufacture credibility
- Deliberately excluded the original author from contributor lists
- Successfully submitted trojanized servers to legitimate MCP registries
Why does this matter?
- Traditional trust signals (GitHub stars, forks, contributor counts) can now be systematically fabricated
- Any organization deploying MCP-enabled AI tools is vulnerable to supply chain compromise
- The payload delivers StealC infostealer targeting developer credentials, browser passwords, cryptocurrency wallets, and Oura Ring health data
- Possible links to China with YuzeHao2023 as primary operator
How Smartloader Built a Fake Github Ecosystem
Unlike opportunistic malware campaigns that prioritize speed and volume, SmartLoader invested months building credibility before deploying their payload. This patient, methodical approach demonstrates the threat actor's understanding that developer trust requires time to manufacture, and their willingness to invest that time for access to high-value targets. The operation unfolded across four carefully orchestrated phases spanning several months:
Phase 1: Target Selection
The attackers identified the Oura MCP Server as their target. The legitimate repository was created 11 months ago by Tomek Korbak, an OpenAI engineer, at:
https://github.com/tomekkorbak/oura-mcp-server
This MCP server connects AI assistants to Oura Ring health data, allowing language models to query sleep patterns, readiness scores, and resilience metrics. The legitimate project description reads:
"A Model Context Protocol (MCP) server that provides access to the Oura API. It allows language models to query sleep, readiness, and resilience data from Oura API."
The attackers selected a target with natural appeal to developers: health optimization tools for productivity-focused tech workers who are precisely the demographic likely to have valuable credentials.
Phase 2: Building the Fake Network (3 Months Ago)
SmartLoader created a network of fake GitHub accounts and populated them with forked repositories to establish apparent legitimacy. The primary account, YuzeHao2023, appears to be the root operator based in China. This account created the initial clean fork (not trojanized):
https://github.com/YuzeHao2023/MCP-oura
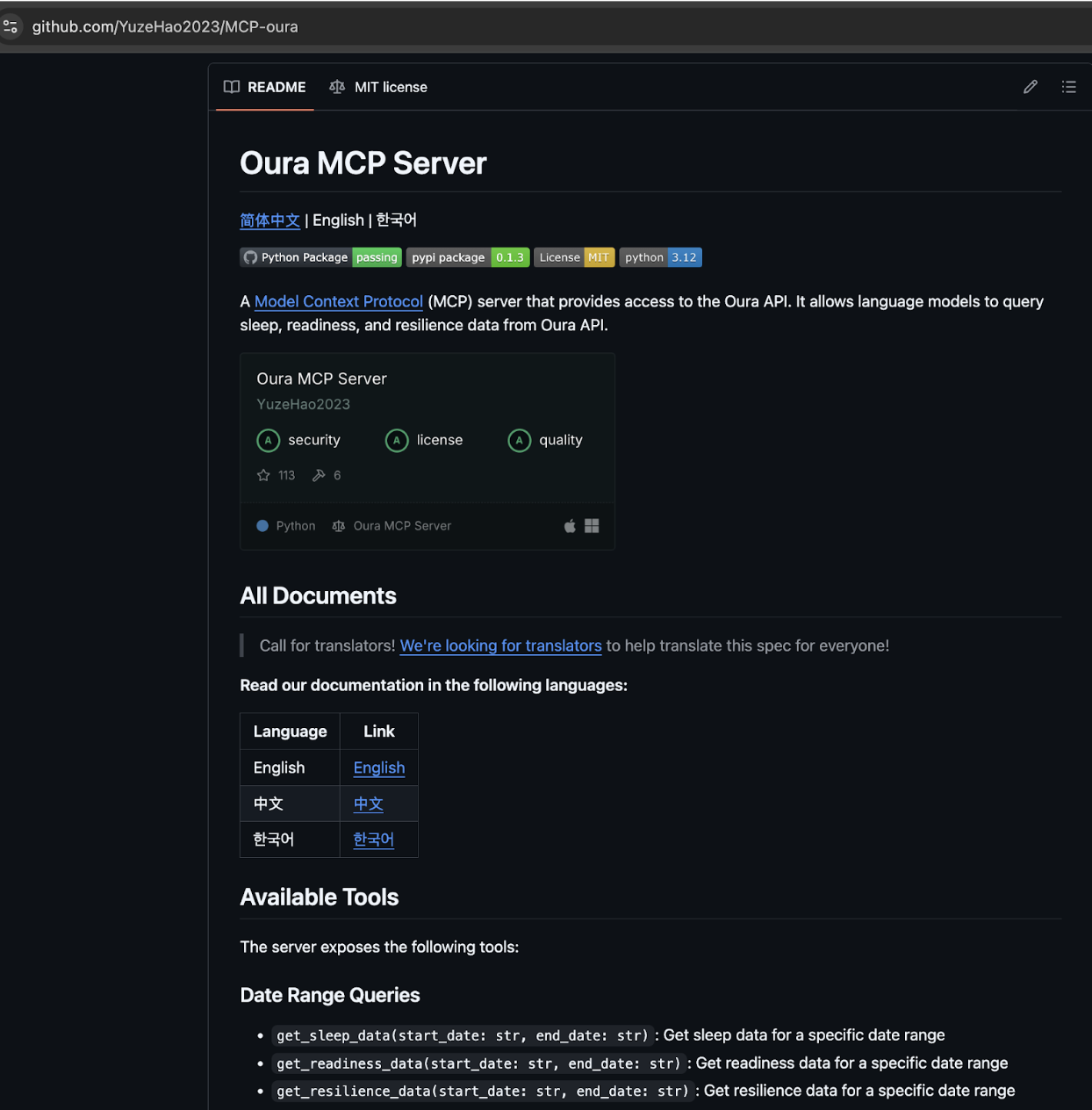
Four additional accounts with same content forked from YuzeHao2023, creating the appearance of organic community interest:
- https://github.com/punkpeye/MCP-oura
- https://github.com/dvlan26/MCP-oura
- https://github.com/halamji/MCP-oura
- https://github.com/yzhao112/MCP-oura
These accounts exhibit characteristics consistent with AI-generated personas: recent creation dates, similar activity patterns, and commits concentrated in the same timeframe. The fake accounts also forked other projects from YuzeHao2023, creating a web of cross-references designed to make each account appear more established.
Phase 3: The Trojanized Repository (2 Months Ago)
With the fake ecosystem in place, the attackers created the payload-carrying repository under a new account:
https://github.com/SiddhiBagul/MCP-oura
In the next Figure, the instructions to install the malware can be seen.
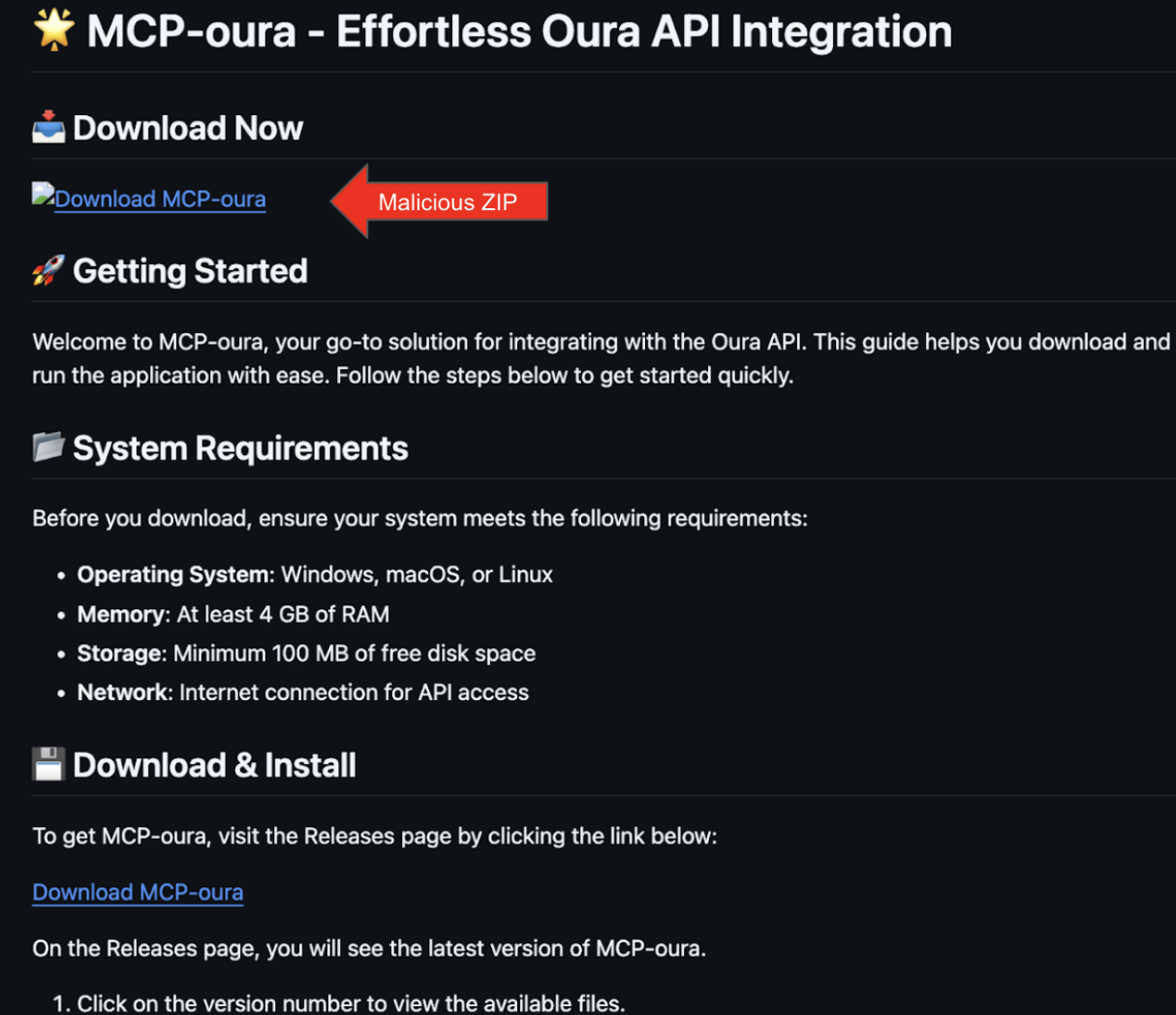
Crucially, they did not add Tomek Korbak—the original author of the legitimate MCP server—as a contributor.This omission is the smoking gun. A legitimate fork would naturally credit the original creator. The deliberate exclusion of the real author while including only the fake accounts confirms coordinated operation by a single threat actor.
Phase 4: Registry Poisoning
The trojanized MCP server was submitted to legitimate MCP registries like MCP Market, where it appeared alongside genuine community contributions. Developers searching for Oura Ring integration would encounter the malicious package with no obvious indicators of compromise because the source code matched the legitimate version, and the contributor list suggested active community involvement.

Attribution: The Smartloader Connection
SmartLoader is an established malware distribution operation known for delivering information stealers through deceptive installers and software cracks. The group has historically targeted users searching for pirated software, using search engine optimization (SEO) poisoning to drive victims to malicious downloads.
This campaign represents a strategic pivot: rather than targeting consumers seeking pirated software, SmartLoader is now targeting developers through supply chain compromise. The shift reflects recognition that developer environments contain high-value assets such as API keys, cloud credentials, cryptocurrency wallets, and access to production systems.
The attack infrastructure and payload characteristics match known SmartLoader tactics, techniques, and procedures (TTPs):
- LuaJIT-based payload delivery
- Virtual machine obfuscation with hundreds of states
- StealC infostealer as final payload
- Scheduled task persistence masquerading as legitimate software (Realtek audio drivers)
- Multi-stage execution chain to evade detection
The China-based operational indicators align with previous SmartLoader attribution, though the group's precise organizational structure remains under investigation.
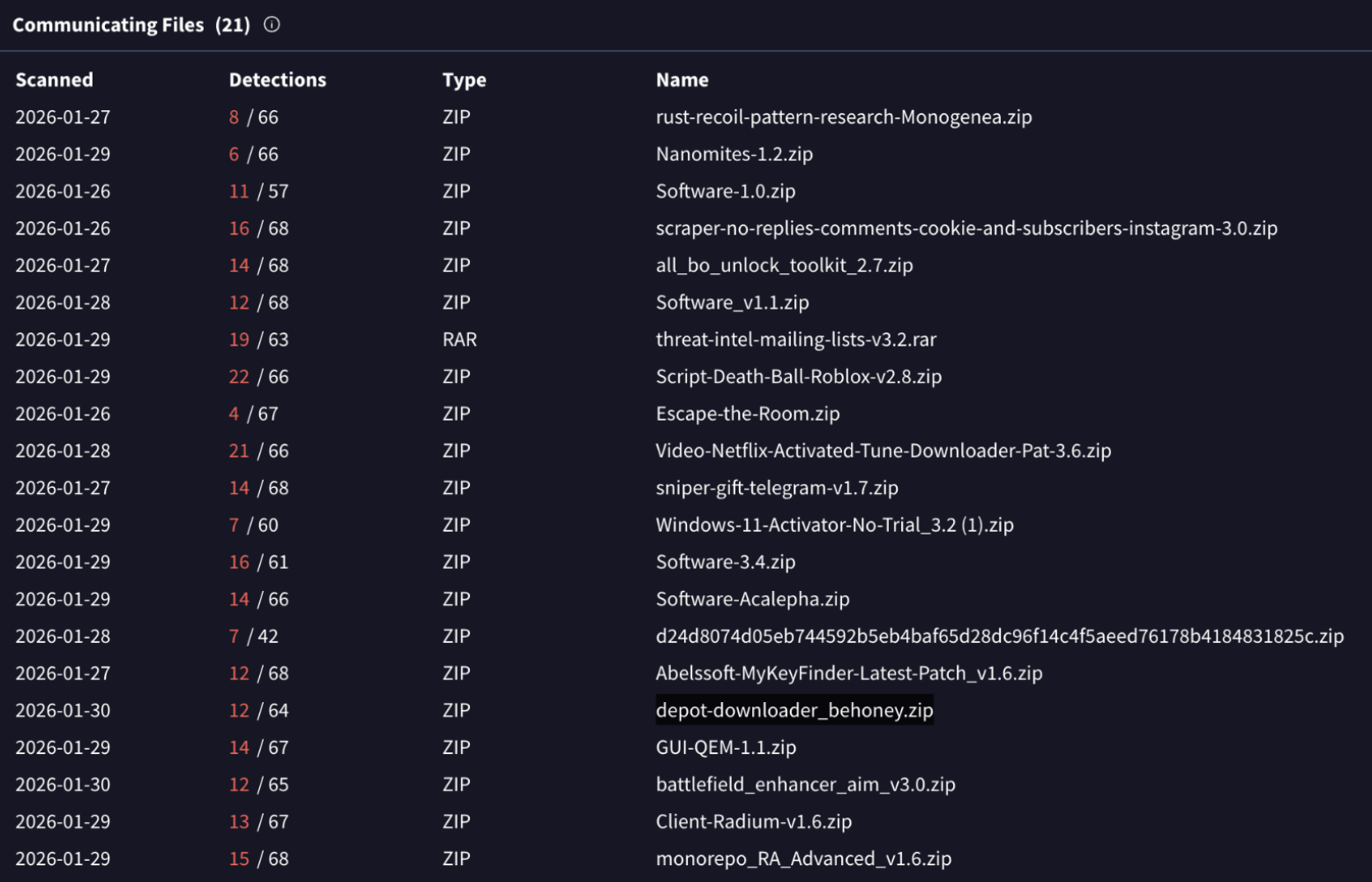
Important to mention that this is an active campaign targeting different industries, here a quick look at the malicious samples delivered by the end of January 2026:
Technical Analysis of SmartLoader's Cloned Oura Ring MCP
Attack Chain Overview
Stage 1 — Initial Delivery
The victim discovers the trojanized MCP server through GitHub search, an MCP registry, or community recommendations. The repository appears legitimate: source code matches the original, multiple contributors are listed, and documentation is complete. The release archive contains an additional file: resource.txt—a heavily obfuscated LuaJIT script.
Stage 2 — Payload Execution
When executed, resource.txt deploys the LuaJIT runtime to two locations in the user's AppData directory:
%LOCALAPPDATA%\ODMw\ODMw.exe
%LOCALAPPDATA%\ODMy\ODMy.exe
The executables are renamed copies of the legitimate LuaJIT interpreter, evading signature-based detection.
Stage 3 — Persistence
The malware creates scheduled tasks disguised as audio driver components:
Task: RealtekAudioManager_ODMw
Executes: ODMw.exe with resource.txt
Task: AudioManager_ODMy
Executes: ODMy.exe with socket3.lua
The Realtek naming convention exploits the ubiquity of Realtek audio drivers on Windows systems. This is because security teams are conditioned to ignore Realtek-related processes.
Stage 4 — StealC Deployment
The socket3.lua payload establishes C2 communication and deploys StealC, which harvests:
- Browser saved passwords and session cookies
- Discord authentication tokens
- Cryptocurrency wallet files and seed phrases
- Cloud service session tokens
- SSH keys and API credentials
Obfuscation Analysis
Straiker researchers employed dynamic instrumentation using Frida to bypass the payload's protections:
Virtual Machine Protection: A custom VM with 443 distinct states transforms program logic into opaque state transitions. Each "instruction" advances through the state machine, making static analysis impractical.
String Encoding: All strings use octal escape sequences assembled at runtime through builder functions. URLs, API endpoints, and configuration values are never present in plaintext.
Chunked Assembly: Sensitive strings are split across multiple variables and concatenated only during execution, defeating string-based detection signatures.
Interesting strings dumped from memory, we can see the known strings related to SmartLoader actions: loader (bypass_defender), tasks (pump), the github used to serve second stage payload and the C2 Server IP:
[STR] {"status":"success","country":"United States","countryCode":"US","region":"CA","regionName":"California","city":"Santa Cruz","zip":"95062","lat":36.9689,"lon":-121.9903,"timezone":"America/Los_Angeles","isp":"Comcast Cable Communications, LLC","org":"Comcast Cable Communications, LLC","as":"AS7922 C
[STR] NTE3YjdjNWU1NjYzNjU2YTA1N2Y
[STR] http://213.176.72.204
[STR] {"bypass_defender": 0, "autorun": 0, "relaunch": {"time": -1, "status": false}, "tablet": {"text": "An error occurred", "status": false}, "hide": 0, "persistence": 1}
[STR] {{"id": 829, "link": "https://github.com/Rayhane106/repo/raw/refs/heads/main/index.html", "file_path": "Temp", "file_name": "socket3.lua", "start": 1, "autorun": 0, "relaunch": 0, "hide": 0, "pump": {"size": -1, "status": false}, "dll_loader": {"func": null, "type": "LoadLibrary"}}, {"id": 830, "lin
[STR] {{["id"]= 829, ["link"]= "https://github.com/Rayhane106/repo/raw/refs/heads/main/index.html", ["file_path"]= "Temp", ["file_name"]= "socket3.lua", ["start"]= 1, ["autorun"]= 0, ["relaunch"]= 0, ["hide"]= 0, ["pump"]= {["size"]= -1, ["status"]= false}, ["dll_loader"]= {["func"]= null, ["type"]= "Load
[STR] ["pump"]= {["size"]= 1024, ["status"]= true}, ["dll_loader"]= {["func"]= null, ["type"]= "LoadLibrary"}}}
A great detailed analysis of this malware can be found on Security Blue Team's blog.
Recommendations for Security Leaders
This campaign exposes fundamental weaknesses in how organizations evaluate AI tooling. SmartLoader's success depends on security teams and developers applying outdated trust heuristics to a new attack surface.
Immediate Actions for CISOs:
- Audit MCP Server Inventory: Determine what MCP servers are installed across your development environments. Most organizations do not have visibility into this category of tooling.
- Establish MCP Vetting Processes: Require security review before MCP server installation, equivalent to your open source dependency review process.
- Verify Provenance Deeply: GitHub stars, forks, and contributor counts can be manufactured. Verify original authorship, check account creation dates, and examine commit history patterns.
- Monitor for Persistence Patterns: The Realtek scheduled task pattern is not unique to this campaign. Hunt for scheduled tasks referencing AppData paths with unusual executables.
- Implement Egress Controls: Block or alert on connections to cryptocurrency RPC endpoints and known malware infrastructure from developer workstations.
Strategic Considerations:
The MCP ecosystem lacks the security infrastructure that has developed around traditional package managers. There is no equivalent to npm audit, Dependabot, or Snyk for MCP servers. Until such tooling matures, organizations must apply manual controls.
Developer workstations represent concentrated risk: credentials, API keys, source code access, and often production system connectivity. Threat actors are increasingly targeting this environment, and the MCP ecosystem provides a new vector for reaching it.
How Straiker Protects Against Rogue MCPs
Straiker recognized the emerging MCP threat surface and developed proactive capabilities to identify rogue servers before they compromise enterprise environments, providing:
- Provenance Analysis: Deep verification of MCP server origins beyond surface-level GitHub metrics. We analyze account creation patterns, commit timing, contributor relationships, and code lineage to identify manufactured trust signals, the exact techniques SmartLoader employed.
- Behavioral Fingerprinting: Runtime analysis of MCP server behavior to detect anomalous network connections, unexpected file system access, and data exfiltration patterns that static analysis misses.
- Registry Monitoring: Continuous scanning of MCP registries for newly published packages matching known malware patterns, suspicious characteristics, or connections to identified threat infrastructure.
- Threat Intelligence Integration: Correlation of MCP server artifacts against our threat intelligence database, including SmartLoader infrastructure and TTPs documented in this report.
- Fake Account Detection: Analysis of contributor networks to identify coordinated inauthentic behavior—the manufactured ecosystem SmartLoader built would trigger multiple detection signals in our system.
Organizations deploying MCP-enabled AI systems require purpose-built security tooling. Traditional AppSec tools were not designed for this attack surface, and manual review does not scale with ecosystem growth.
For our customers, the detection is deployed in the platform as STRK.MCP.AiPT.SmartLoader:
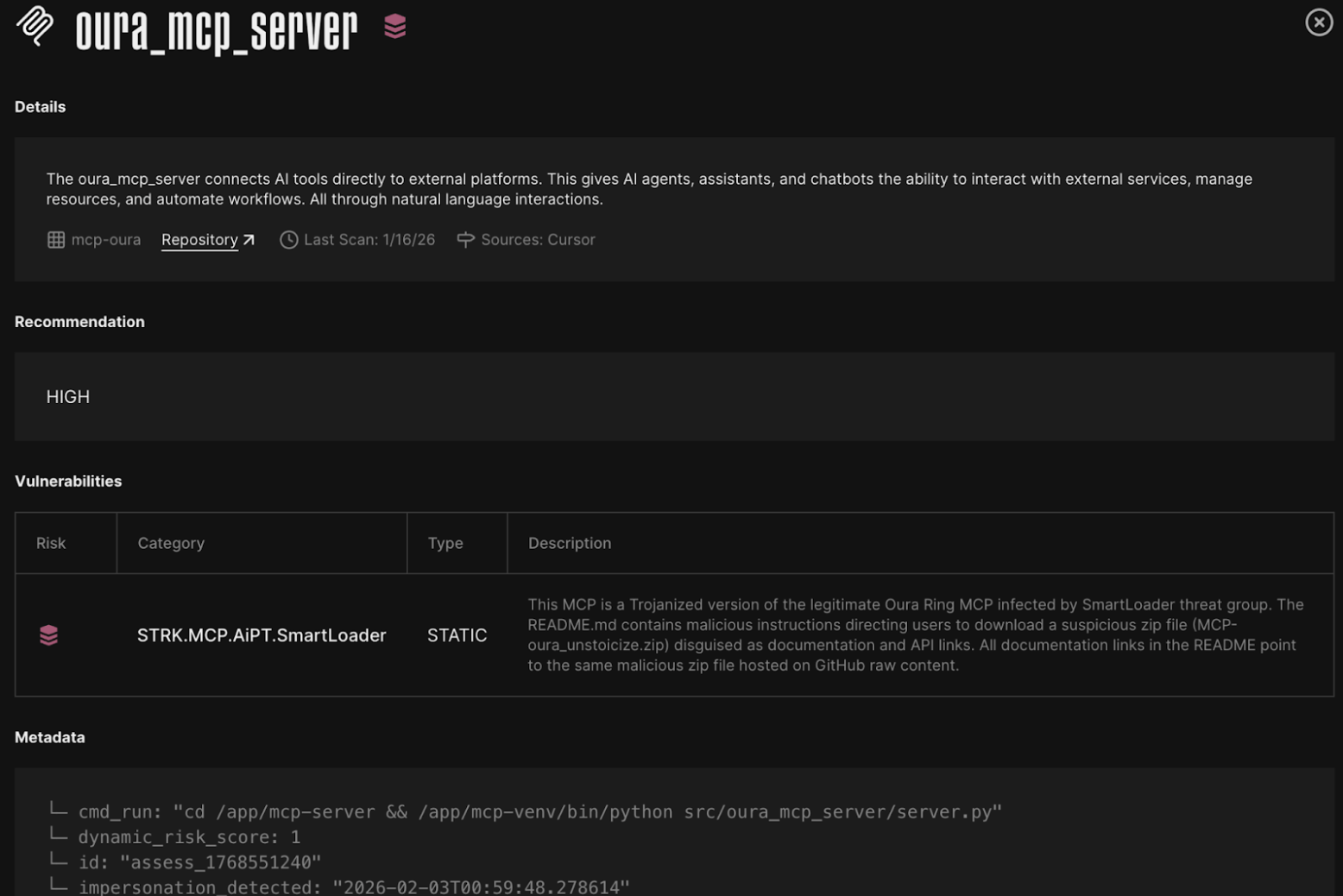
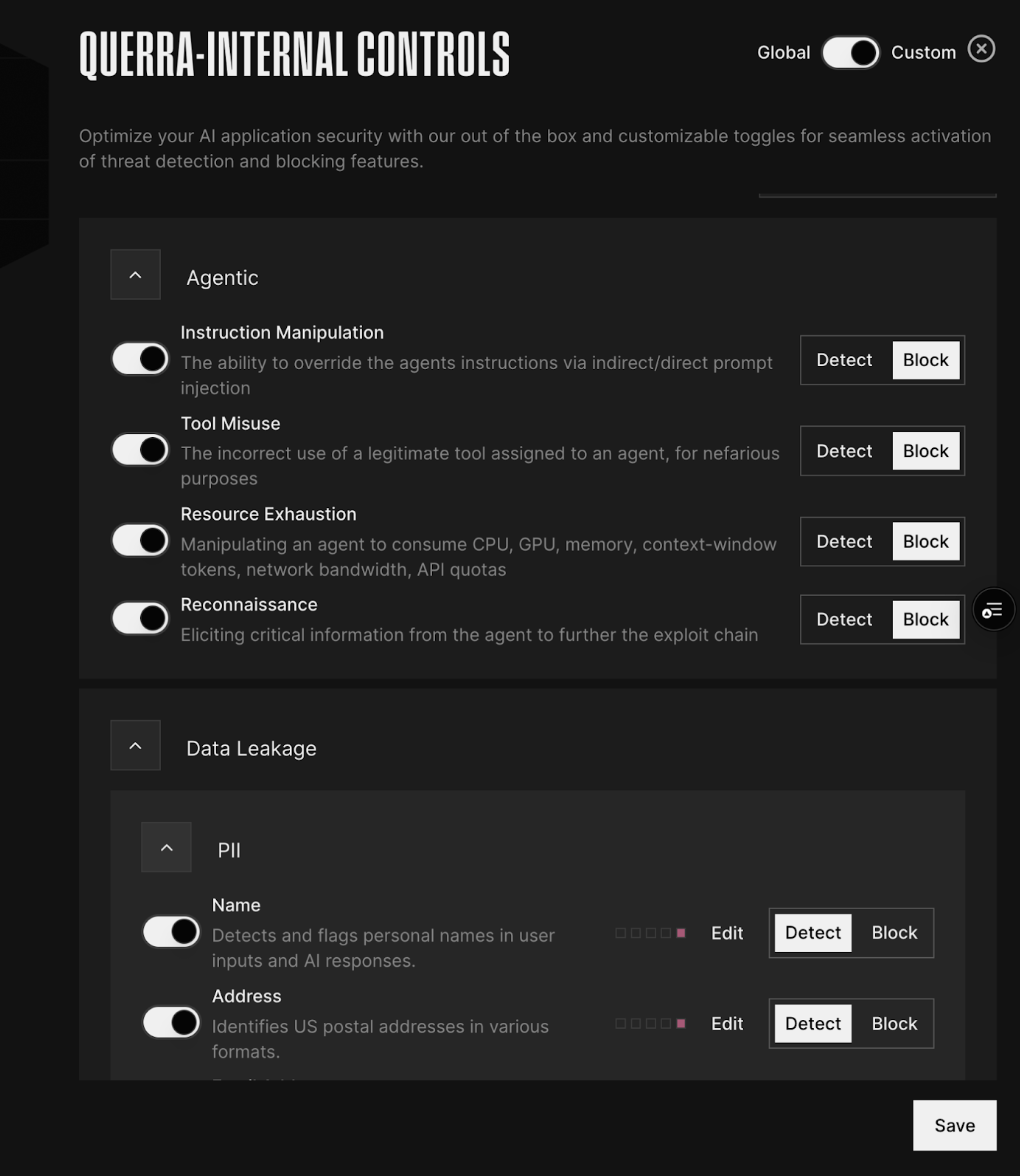
Straiker’s AI engine detects and blocks runtime risks introduced through MCP tool integrations with agents. MCP-based attack techniques, such as tool poisoning and rug pulling, can manipulate agents into executing malicious or unintended actions. By enforcing the controls below, Straiker prevents these runtime threats and ensures safe agent-tool interactions. Straiker also can integrate with your existing security products for remediation and response.
Conclusion
SmartLoader's campaign against the MCP ecosystem should serve as a wake-up call for security leaders. Threat actors have moved beyond opportunistic malware distribution and they are now investing in elaborate social engineering infrastructure to compromise developer supply chains.
The construction of fake GitHub accounts, manufactured fork networks, and strategic contributor manipulation demonstrates a level of sophistication that demands equally sophisticated defenses. Casual inspection of repository metrics is no longer adequate due diligence.
As AI assistants become integral to enterprise workflows, the MCP servers that extend their capabilities become a critical attack surface. Organizations that fail to secure this vector expose themselves to credential theft, data exfiltration, and supply chain compromise.
Straiker remains committed to proactive identification of threats to the AI ecosystem. We will continue publishing intelligence to help the security community stay ahead of emerging attack techniques.
For organizations seeking to assess their MCP security posture or evaluate exposure to this campaign, Straiker offers complimentary threat assessments. Contact our team to secure your AI infrastructure before threat actors find your blind spots.
Signal Check ⚡️
EXECUTIVE SUMMARY OF FINDINGS
Straiker's AI Research (STAR) Labs team has uncovered a trojanized MCP server targeting Oura Ring health data and successfully infiltrated legitimate Model Context Protocol (MCP) registries, exposing thousands of developers and end-users to credential theft and data compromise. SmartLoader, an established malware operation known for distributing info-stealers through deceptive installers, first discovered early in 2024, has constructed an elaborate network of fake GitHub accounts and repositories to distribute trojanized MCP servers, successfully poisoning legitimate MCP registries in the process.
Our investigation revealed the threat actors cloned a legitimate Oura MCP Server—a tool that connects AI assistants to Oura Ring health data—and built a deceptive infrastructure of fake forks and contributors to manufacture credibility. The trojanized version of the Oura MCP server delivers the StealC infostealer, targeting developer credentials, browser passwords, and cryptocurrency wallets.
This campaign signals a significant shift in the threat landscape: traditional threat actors who have long targeted software supply chains are now pivoting to MCP ecosystems, bringing their proven tactics and operational sophistication to this emerging attack surface.
Key Findings:
What happened? SmartLoader poisoned legitimate MCP registries with a trojanized Oura MCP Server designed to steal credentials, cryptocurrency, and health data.
How did they do it?
- Created at least 5 fake GitHub accounts to build a network of seemingly legitimate repository forks
- Added fake accounts as "contributors" to manufacture credibility
- Deliberately excluded the original author from contributor lists
- Successfully submitted trojanized servers to legitimate MCP registries
Why does this matter?
- Traditional trust signals (GitHub stars, forks, contributor counts) can now be systematically fabricated
- Any organization deploying MCP-enabled AI tools is vulnerable to supply chain compromise
- The payload delivers StealC infostealer targeting developer credentials, browser passwords, cryptocurrency wallets, and Oura Ring health data
- Possible links to China with YuzeHao2023 as primary operator
How Smartloader Built a Fake Github Ecosystem
Unlike opportunistic malware campaigns that prioritize speed and volume, SmartLoader invested months building credibility before deploying their payload. This patient, methodical approach demonstrates the threat actor's understanding that developer trust requires time to manufacture, and their willingness to invest that time for access to high-value targets. The operation unfolded across four carefully orchestrated phases spanning several months:
Phase 1: Target Selection
The attackers identified the Oura MCP Server as their target. The legitimate repository was created 11 months ago by Tomek Korbak, an OpenAI engineer, at:
https://github.com/tomekkorbak/oura-mcp-server
This MCP server connects AI assistants to Oura Ring health data, allowing language models to query sleep patterns, readiness scores, and resilience metrics. The legitimate project description reads:
"A Model Context Protocol (MCP) server that provides access to the Oura API. It allows language models to query sleep, readiness, and resilience data from Oura API."
The attackers selected a target with natural appeal to developers: health optimization tools for productivity-focused tech workers who are precisely the demographic likely to have valuable credentials.
Phase 2: Building the Fake Network (3 Months Ago)
SmartLoader created a network of fake GitHub accounts and populated them with forked repositories to establish apparent legitimacy. The primary account, YuzeHao2023, appears to be the root operator based in China. This account created the initial clean fork (not trojanized):
https://github.com/YuzeHao2023/MCP-oura

Four additional accounts with same content forked from YuzeHao2023, creating the appearance of organic community interest:
- https://github.com/punkpeye/MCP-oura
- https://github.com/dvlan26/MCP-oura
- https://github.com/halamji/MCP-oura
- https://github.com/yzhao112/MCP-oura
These accounts exhibit characteristics consistent with AI-generated personas: recent creation dates, similar activity patterns, and commits concentrated in the same timeframe. The fake accounts also forked other projects from YuzeHao2023, creating a web of cross-references designed to make each account appear more established.
Phase 3: The Trojanized Repository (2 Months Ago)
With the fake ecosystem in place, the attackers created the payload-carrying repository under a new account:
https://github.com/SiddhiBagul/MCP-oura
In the next Figure, the instructions to install the malware can be seen.

Crucially, they did not add Tomek Korbak—the original author of the legitimate MCP server—as a contributor.This omission is the smoking gun. A legitimate fork would naturally credit the original creator. The deliberate exclusion of the real author while including only the fake accounts confirms coordinated operation by a single threat actor.
Phase 4: Registry Poisoning
The trojanized MCP server was submitted to legitimate MCP registries like MCP Market, where it appeared alongside genuine community contributions. Developers searching for Oura Ring integration would encounter the malicious package with no obvious indicators of compromise because the source code matched the legitimate version, and the contributor list suggested active community involvement.

Attribution: The Smartloader Connection
SmartLoader is an established malware distribution operation known for delivering information stealers through deceptive installers and software cracks. The group has historically targeted users searching for pirated software, using search engine optimization (SEO) poisoning to drive victims to malicious downloads.
This campaign represents a strategic pivot: rather than targeting consumers seeking pirated software, SmartLoader is now targeting developers through supply chain compromise. The shift reflects recognition that developer environments contain high-value assets such as API keys, cloud credentials, cryptocurrency wallets, and access to production systems.
The attack infrastructure and payload characteristics match known SmartLoader tactics, techniques, and procedures (TTPs):
- LuaJIT-based payload delivery
- Virtual machine obfuscation with hundreds of states
- StealC infostealer as final payload
- Scheduled task persistence masquerading as legitimate software (Realtek audio drivers)
- Multi-stage execution chain to evade detection
The China-based operational indicators align with previous SmartLoader attribution, though the group's precise organizational structure remains under investigation.
Important to mention that this is an active campaign targeting different industries, here a quick look at the malicious samples delivered by the end of January 2026:

Technical Analysis of SmartLoader's Cloned Oura Ring MCP
Attack Chain Overview
Stage 1 — Initial Delivery
The victim discovers the trojanized MCP server through GitHub search, an MCP registry, or community recommendations. The repository appears legitimate: source code matches the original, multiple contributors are listed, and documentation is complete. The release archive contains an additional file: resource.txt—a heavily obfuscated LuaJIT script.
Stage 2 — Payload Execution
When executed, resource.txt deploys the LuaJIT runtime to two locations in the user's AppData directory:
%LOCALAPPDATA%\ODMw\ODMw.exe
%LOCALAPPDATA%\ODMy\ODMy.exe
The executables are renamed copies of the legitimate LuaJIT interpreter, evading signature-based detection.
Stage 3 — Persistence
The malware creates scheduled tasks disguised as audio driver components:
Task: RealtekAudioManager_ODMw
Executes: ODMw.exe with resource.txt
Task: AudioManager_ODMy
Executes: ODMy.exe with socket3.lua
The Realtek naming convention exploits the ubiquity of Realtek audio drivers on Windows systems. This is because security teams are conditioned to ignore Realtek-related processes.
Stage 4 — StealC Deployment
The socket3.lua payload establishes C2 communication and deploys StealC, which harvests:
- Browser saved passwords and session cookies
- Discord authentication tokens
- Cryptocurrency wallet files and seed phrases
- Cloud service session tokens
- SSH keys and API credentials
Obfuscation Analysis
Straiker researchers employed dynamic instrumentation using Frida to bypass the payload's protections:
Virtual Machine Protection: A custom VM with 443 distinct states transforms program logic into opaque state transitions. Each "instruction" advances through the state machine, making static analysis impractical.
String Encoding: All strings use octal escape sequences assembled at runtime through builder functions. URLs, API endpoints, and configuration values are never present in plaintext.
Chunked Assembly: Sensitive strings are split across multiple variables and concatenated only during execution, defeating string-based detection signatures.
Interesting strings dumped from memory, we can see the known strings related to SmartLoader actions: loader (bypass_defender), tasks (pump), the github used to serve second stage payload and the C2 Server IP:
[STR] {"status":"success","country":"United States","countryCode":"US","region":"CA","regionName":"California","city":"Santa Cruz","zip":"95062","lat":36.9689,"lon":-121.9903,"timezone":"America/Los_Angeles","isp":"Comcast Cable Communications, LLC","org":"Comcast Cable Communications, LLC","as":"AS7922 C
[STR] NTE3YjdjNWU1NjYzNjU2YTA1N2Y
[STR] http://213.176.72.204
[STR] {"bypass_defender": 0, "autorun": 0, "relaunch": {"time": -1, "status": false}, "tablet": {"text": "An error occurred", "status": false}, "hide": 0, "persistence": 1}
[STR] {{"id": 829, "link": "https://github.com/Rayhane106/repo/raw/refs/heads/main/index.html", "file_path": "Temp", "file_name": "socket3.lua", "start": 1, "autorun": 0, "relaunch": 0, "hide": 0, "pump": {"size": -1, "status": false}, "dll_loader": {"func": null, "type": "LoadLibrary"}}, {"id": 830, "lin
[STR] {{["id"]= 829, ["link"]= "https://github.com/Rayhane106/repo/raw/refs/heads/main/index.html", ["file_path"]= "Temp", ["file_name"]= "socket3.lua", ["start"]= 1, ["autorun"]= 0, ["relaunch"]= 0, ["hide"]= 0, ["pump"]= {["size"]= -1, ["status"]= false}, ["dll_loader"]= {["func"]= null, ["type"]= "Load
[STR] ["pump"]= {["size"]= 1024, ["status"]= true}, ["dll_loader"]= {["func"]= null, ["type"]= "LoadLibrary"}}}
A great detailed analysis of this malware can be found on Security Blue Team's blog.
Recommendations for Security Leaders
This campaign exposes fundamental weaknesses in how organizations evaluate AI tooling. SmartLoader's success depends on security teams and developers applying outdated trust heuristics to a new attack surface.
Immediate Actions for CISOs:
- Audit MCP Server Inventory: Determine what MCP servers are installed across your development environments. Most organizations do not have visibility into this category of tooling.
- Establish MCP Vetting Processes: Require security review before MCP server installation, equivalent to your open source dependency review process.
- Verify Provenance Deeply: GitHub stars, forks, and contributor counts can be manufactured. Verify original authorship, check account creation dates, and examine commit history patterns.
- Monitor for Persistence Patterns: The Realtek scheduled task pattern is not unique to this campaign. Hunt for scheduled tasks referencing AppData paths with unusual executables.
- Implement Egress Controls: Block or alert on connections to cryptocurrency RPC endpoints and known malware infrastructure from developer workstations.
Strategic Considerations:
The MCP ecosystem lacks the security infrastructure that has developed around traditional package managers. There is no equivalent to npm audit, Dependabot, or Snyk for MCP servers. Until such tooling matures, organizations must apply manual controls.
Developer workstations represent concentrated risk: credentials, API keys, source code access, and often production system connectivity. Threat actors are increasingly targeting this environment, and the MCP ecosystem provides a new vector for reaching it.
How Straiker Protects Against Rogue MCPs
Straiker recognized the emerging MCP threat surface and developed proactive capabilities to identify rogue servers before they compromise enterprise environments, providing:
- Provenance Analysis: Deep verification of MCP server origins beyond surface-level GitHub metrics. We analyze account creation patterns, commit timing, contributor relationships, and code lineage to identify manufactured trust signals, the exact techniques SmartLoader employed.
- Behavioral Fingerprinting: Runtime analysis of MCP server behavior to detect anomalous network connections, unexpected file system access, and data exfiltration patterns that static analysis misses.
- Registry Monitoring: Continuous scanning of MCP registries for newly published packages matching known malware patterns, suspicious characteristics, or connections to identified threat infrastructure.
- Threat Intelligence Integration: Correlation of MCP server artifacts against our threat intelligence database, including SmartLoader infrastructure and TTPs documented in this report.
- Fake Account Detection: Analysis of contributor networks to identify coordinated inauthentic behavior—the manufactured ecosystem SmartLoader built would trigger multiple detection signals in our system.
Organizations deploying MCP-enabled AI systems require purpose-built security tooling. Traditional AppSec tools were not designed for this attack surface, and manual review does not scale with ecosystem growth.
For our customers, the detection is deployed in the platform as STRK.MCP.AiPT.SmartLoader:

Straiker’s AI engine detects and blocks runtime risks introduced through MCP tool integrations with agents. MCP-based attack techniques, such as tool poisoning and rug pulling, can manipulate agents into executing malicious or unintended actions. By enforcing the controls below, Straiker prevents these runtime threats and ensures safe agent-tool interactions. Straiker also can integrate with your existing security products for remediation and response.

Conclusion
SmartLoader's campaign against the MCP ecosystem should serve as a wake-up call for security leaders. Threat actors have moved beyond opportunistic malware distribution and they are now investing in elaborate social engineering infrastructure to compromise developer supply chains.
The construction of fake GitHub accounts, manufactured fork networks, and strategic contributor manipulation demonstrates a level of sophistication that demands equally sophisticated defenses. Casual inspection of repository metrics is no longer adequate due diligence.
As AI assistants become integral to enterprise workflows, the MCP servers that extend their capabilities become a critical attack surface. Organizations that fail to secure this vector expose themselves to credential theft, data exfiltration, and supply chain compromise.
Straiker remains committed to proactive identification of threats to the AI ecosystem. We will continue publishing intelligence to help the security community stay ahead of emerging attack techniques.
For organizations seeking to assess their MCP security posture or evaluate exposure to this campaign, Straiker offers complimentary threat assessments. Contact our team to secure your AI infrastructure before threat actors find your blind spots.
Related Resources
Click to Open File
similar resources

Secure your agentic AI and AI-native application journey with Straiker
.avif)













